How to Protect Your WordPress Site Against Zero Day Vulnerabilities (7 Tips)
Security threats come in all shapes and sizes, but there’s one piece of advice that’s always relevant: install the latest update. However, sometimes there’s no security patch available, because you and the software vendor are alerted to the vulnerability at the same time.
Fortunately, there are still ways to keep your website safe. By implementing some best practices, you can harden your WordPress site against all manner of attacks, including the dreaded zero day vulnerability.
In this post, we’ll take a closer look at this security threat, and why it’s taken so seriously among the WordPress community. We’ll then show you how to achieve the near-impossible and protect your site against vulnerabilities that haven’t even been discovered yet. Let’s get started!
An Introduction to Zero Day Vulnerabilities
Zero day vulnerabilities immediately stand out due to their distinctive name. We can trace the term “zero day“ all the way back to the 1990s, when pirates shared commercial software illegally via bulletin boards.
The community categorized this pirated software by days. For example, if a particular piece of software had been publicly available for 50 days, they referred to it as 50-day software.
Zero day referred to software that hadn’t been officially released to the public. Typically, zero day code was acquired by hacking into the vendor’s network and stealing the unreleased program. Sometimes, an insider would leak the code.
The security industry has repurposed this term to indicate a vulnerability that’s known to the vendor, but that a patch isn’t available for yet. In other words, the security loophole is putting users at risk and the vendor has zero days to solve the problem.
“Window of Vulnerability (WoV)” is another term that we often use alongside zero day. This is the period of time between a vendor learning about the vulnerability and them releasing a patch to the public.
The final related term that’s often associated with zero day vulnerabilities is “forever day vulnerability”. Here, everyone knows about a security loophole and the original developer has no intention to fix it.
This usually occurs because the software is no longer being actively maintained. If the project in question is open source, then there may be some scope to delve into the code and fix the problem yourself. However, as a general rule, it’s wise to look for software that’s still under active development.
The Life Cycle of a Zero Day Vulnerability
The way the community discovers and manages vulnerabilities can vary. However, it typically starts with a researcher or a malicious third party discovering a security issue. At this point, the vulnerability is considered zero day, as it’s known but no fix is available. This is also the start of the WoV.
The vendor may not always publicly acknowledge that there’s a zero day vulnerability affecting its software. While this may be worrying for those who use this program, it’s a tactical decision to help protect as many people as possible.
If a vendor announced that their software is vulnerable and there’s currently no fix available, they’re essentially alerting hackers to a serious security issue. This can cause a spike in attacks.
Hopefully, the vendor will develop a fix in record time. They can then release a patch either as part of a regularly-scheduled update, or as an emergency fix.
At this point, the WoV ends. Assuming that you install the security update, your website is no longer at risk from this particular vulnerability.
Why It’s Important to Protect Your WordPress Website
WordPress now powers over 40 percent of the web. While this popularity speaks volumes about its strength as a Content Management System (CMS), it also makes WordPress a prime target for hackers. If a malicious third party managed to uncover a zero day vulnerability in WordPress, it could potentially weaponize this single weak spot against millions of websites.
There’s plenty of evidence to indicate that hackers are actively targeting WordPress vulnerabilities. In fact, Wordfence recorded 4.3 billion attempts to exploit these loopholes in a single year. Sadly, many of these attacks are successful. When Patchstack spoke to the WordPress community about security, it discovered that 25 percent of respondents had recently dealt with a hacked site.
If a malicious third party does manage to gain unauthorized access to your site, the consequences could be disastrous. The attacker might deface your site, trick your visitors into downloading viruses, or redirect them to a spammy website. All of these actions can damage your reputation. They may even continue to affect your traffic and conversion rates long after you’ve addressed the hack.
Even worse, the attacker might delete or even steal your data. If you run an e-commerce site, this might include your customers’ credit or debit card details. This kind of Public Relations (PR) disaster can have huge financial implications, with the average total cost of a data breach coming in at $3.86 million.
Depending on your geographical location and the nature of the breach, it may even land you in legal hot water. If a court decides that you didn’t take adequate steps to protect your audience’s data, it could result in a hefty fine.
How to Protect Your Site Against Zero Day Vulnerabilities (7 Tips)
When a vendor announces a new zero day vulnerability, speed is everything. To help you leap into action, here are seven tips for hardening your site against the dreaded zero day vulnerability.
1. Check for Updates
As soon as a developer discovers a vulnerability, the clock starts ticking. The good news is that responsible vendors and developers take security threats very seriously, and most of them will start working on a fix right away.
Whenever you hear about a zero day threat, it’s smart to ensure that you’re running the very latest release of the affected software. You may even discover that a patch is already available.
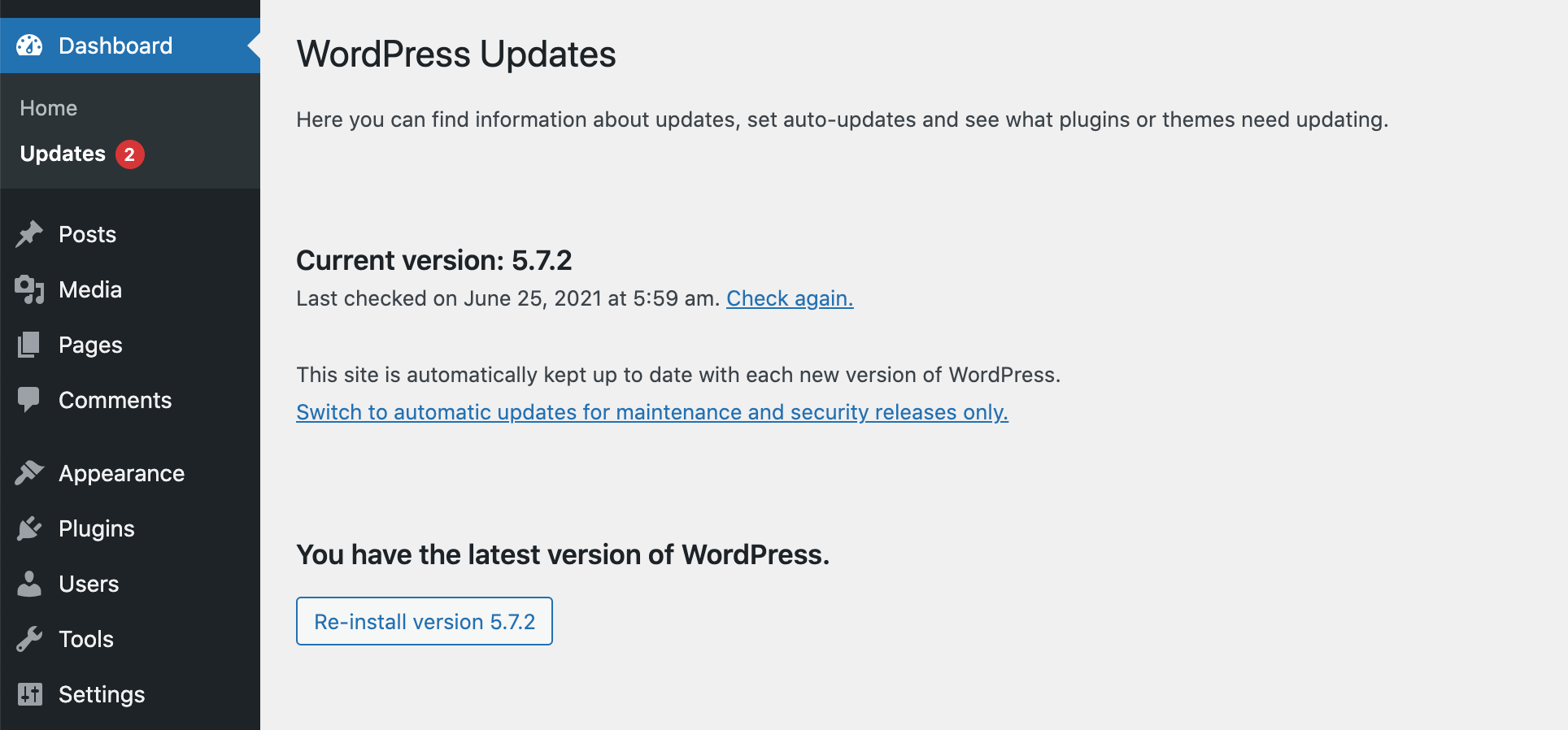
To check for updates to WordPress core, navigate to Dashboard > Updates. If a new release is available, then you can follow the onscreen instructions to download and install it.
Even if the dashboard confirms that you’re fully up-to-date, it’s still worth clicking on Check again, just to verify that you are running the latest release:
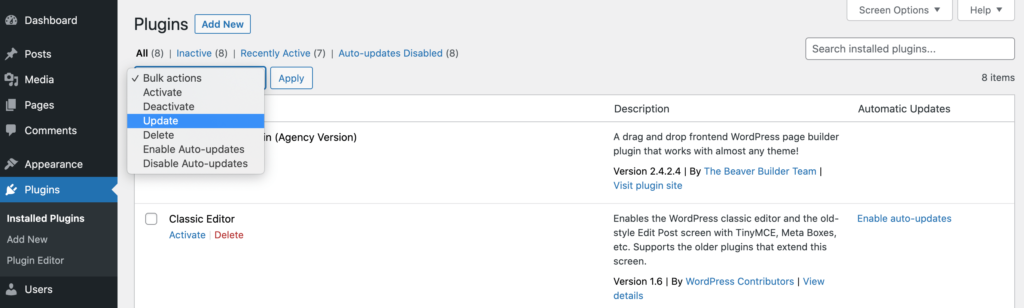
To check your plugins, select Plugins from the WordPress dashboard and then install any available updates. You can also update your plugins en masse using the Bulk Actions dropdown:
Even if a patch isn’t available, chances are that a fix is imminent. For this reason, you may want to consider enabling auto-updates.
To automatically update WordPress core, navigate to Dashboard > Updates. You can then select the following link: Enable automatic updates for all new versions of WordPress. Now, WordPress will automatically download and install all minor and major releases.
To auto-update your plugins, navigate to Plugins > Installed Plugins. You can then select the Plugin checkbox. Next, open the Bulk Actions dropdown and select Enable Auto-Updates > Apply.
Finally, you can enable auto-updates for your WordPress theme. To make this change, navigate to Appearance > Themes. Then hover over your active theme, and select Theme Details:
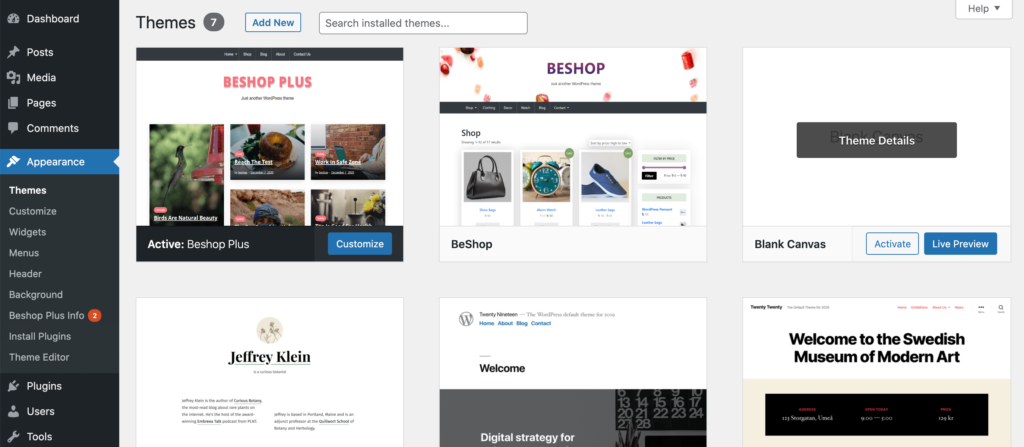
On the subsequent screen, select Enable auto-updates. Your theme will now update automatically as soon as a new version becomes available.
2. Disable the Theme or Plugin
Zero day threats can affect any project, including WordPress core. However, themes and plugins are more susceptible to security issues.
In its 2021 report, WP White Security identified almost 4,000 WordPress plugin vulnerabilities. Patchstack supports this discovery, with their report concluding that over 70 million WordPress websites are running vulnerable plugins and themes.
Fortunately, zero day threats in themes and plugins are often easier to manage when compared to issues with WordPress core. If the original developer hasn’t released a patch yet, you always have the option to delete the theme or plugin that contains the vulnerability.
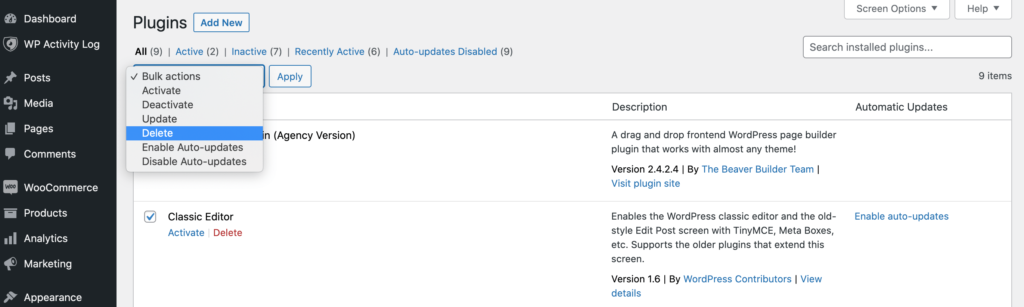
It’s worth noting that disabling this software isn’t always enough. Malicious third parties may still be able to access and exploit sensitive files, even when the plugin or theme is deactivated. For this reason, we always recommend disabling and then deleting the software in question:
Some themes and plugins are business-critical. If your site depends on a particular piece of software, then deleting it may not always be straightforward.
However, WordPress has a huge community of third-party software, so it’s not uncommon for multiple themes and plugins to deliver identical end results. Even if you’re not prepared to give up on a particular program, you may be able to remove it temporarily, and then replace it with an equivalent WordPress plugin or similar theme.
3. Use a Firewall
Many security programs rely on pattern matching to successfully identify and block vulnerabilities. However, they need to know what they’re looking for. Even the best software may struggle to defend against a newly-identified threat.
This doesn’t mean your site is defenseless. Your security software can still block the attacks that are produced as a result of someone exploiting a zero day vulnerability. In particular, a firewall can defend your WordPress website against many common attacks, including Structured Query Language (SQL) injections, and Cross-Site Scripting (XSS) attacks.
When it comes to firewalls, you have several options. If you have an unmanaged Virtual Private Server (VPS), a cloud VPS, or an unmanaged dedicated server, you can secure your system using an Advanced Policy Firewall (APF). This enables you to grant and deny access based on IP addresses.
Alternatively, you can create IP-based access rules using iptables. You can also use the iptables utility program to grant and deny access to selected devices. This gives you complete control over everything that goes in and out of your server, including Transmission Control Protocol (TCP) and Secure Shell (SSH) connections.
Another option is to use a plugin such as Wordfence Security. This Web Application Firewall (WAF) checks your site’s core files, themes, and plugins for malware. It also monitors your site for malicious redirects and code injections, which can indicate an underlying zero day vulnerability:

To prevent false positives, it’s important to place Wordfence in Learning Mode for at least a week after activating its firewall. This allows the plugin to collect all the data it needs to defend your site, without wrongly flagging legitimate actions as suspicious.
4. Monitor Your Site for Suspicious Behavior
Similar to a firewall, a security log cannot directly protect your site against zero day vulnerabilities. However, it may help you identify suspicious behavior and traffic.
WP Activity Log is a popular plugin that records various activities. Every time someone makes a change to your WordPress settings, themes, plugins, or database, this plugin will add it to your activity log:
The WP Activity Log plugin will also record any multisite network changes. This includes adding, deleting, or archiving sites, as well as removing users.
If anyone creates, modifies, or deletes any of your WordPress files, this will also appear in your activity log. If you’re using the free version, you can view the activity log at any point by navigating to WP Activity Log > Log View:
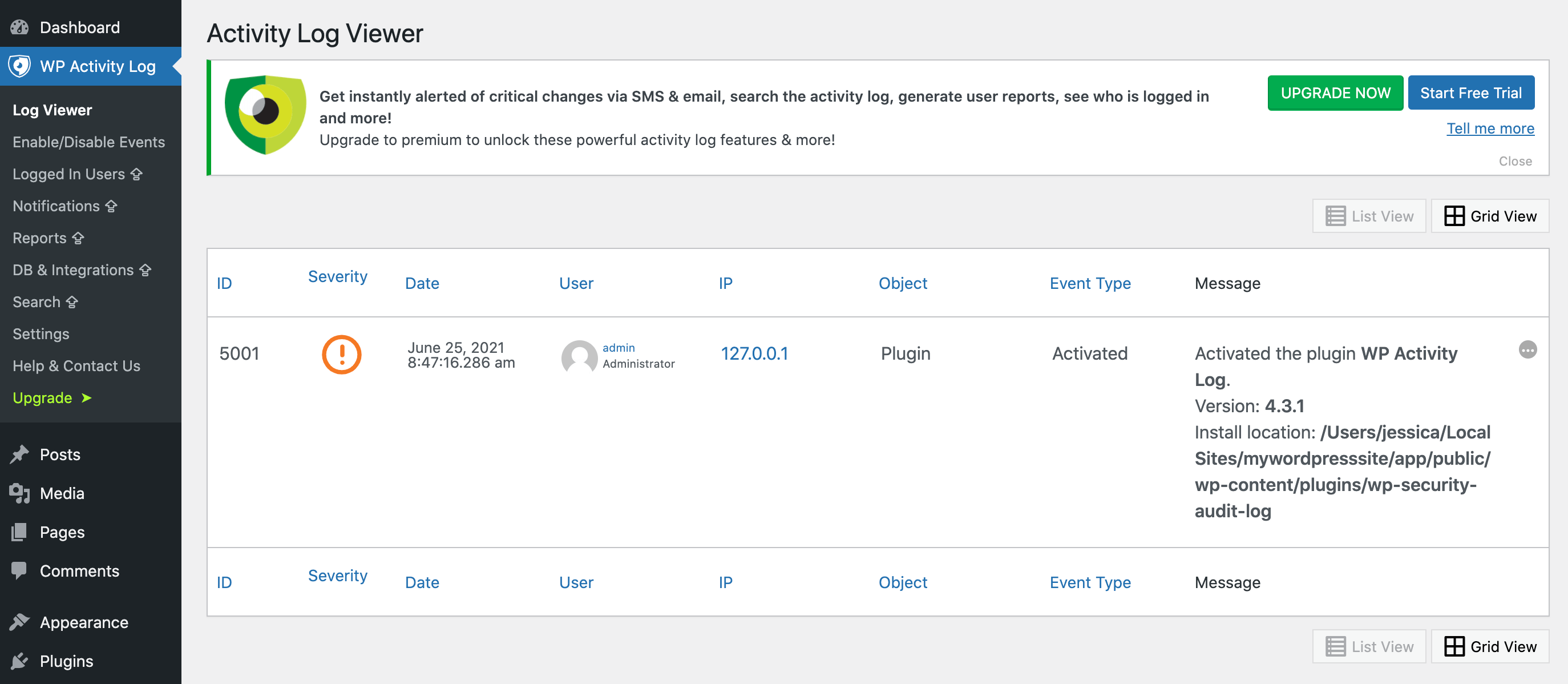
However, this relies on you manually checking the Log View. This may result in a delay between the suspicious behavior occurring and you realizing that there’s a potential security threat.
If you upgrade to Premium, WP Activity Log will send you an SMS or email notification every time someone makes an important change to your website. This puts you in a stronger position to respond to attacks as soon as they occur.
5. Keep Up-to-Date With the Latest Security News
Whenever a vendor discovers a security threat, they’ll notify the affected parties via a vulnerability disclosure. This process is controversial and the subject of frequent debate, as keeping the majority of users safe often means delaying the announcement until a fix is available.
This can minimize the number of would-be hackers who are aware of the security loophole. However, it also means that you may be unknowingly running insecure software on your website.
There’s also the issue of security researchers, who are often the ones who discover these vulnerabilities. Publicly announcing that they’ve identified a security loophole is great advertisement for them. Despite this incentive, most responsible security researchers reach an agreement with the vendor. This often involves delaying publishing their report until a solution is found.
However, some zero day vulnerabilities are announced before a patch is released. Even worse, sometimes a security loophole becomes public knowledge without the vendor being notified in advance. This is particularly common when a malicious third party is the first to discover the loophole. These people will typically want as many hackers as possible to profit from their discovery.
Regardless of your stance on the subject, if a vulnerability does become common knowledge then you’ll want to know about it. To keep you finger on the pulse of WordPress security, it helps to follow popular blogs such as Sucuri WordPress Security, the official WordPress blog, and the Wordfence blog:
For up-to-the-minute updates, it may also help to follow these sites on social media, or you might subscribe to the WP Security Blogger aggregator. Another option is to create a Google Alert for words and phrases related to WordPress security.
6. Join a Disclosure Mailing List
There are many different mailing lists that are dedicated to sharing vulnerability disclosures, but one of the most widely-known is Full Disclosure. By joining this mailing list, you’ll receive email notifications about the latest security threats:
However, Full Disclosure isn’t a WordPress-specific list, so you may get overwhelmed by updates. Assuming that you’re only interested in threats to the WordPress platform, we recommend setting up some email filters.
This can ensure that when you do receive a Full Disclosure notification, you’ll be able to act on it immediately. Similarly, you may also want to subscribe to Wordfence’s WordPress Security Mailing List.
7. Choose a Secure Hosting Provider
No hosting provider can promise to make your site immune to as-yet-undiscovered vulnerabilities. However, a good host will have security features that make it more difficult for attackers to capitalize on these weak spots.
Let’s look at an example. A hacker might attempt to use a zero day vulnerability to launch an XSS attack against your site. Your hosting provider may be completely unaware of this brand-new security loophole. However, they may still be able to stop the XSS attack. This will prevent the hacker from damaging your site or stealing your data.
At A2 Hosting, all of our hosting packages have a range of built-in security features, including HackScan Protection. This can help block malicious third parties before they can inflict serious damage on your website:
We also offer KernelCare rebootless updates and a dual firewall, and provide Cloudflare as a standard CDN. Cloudflare in particular can identify and stop malicious requests in their tracks. This includes requests that may be trying to exploit zero day vulnerabilities.
Conclusion
It’s impossible to predict the future, which means it isn’t easy to prepare for zero day vulnerabilities. Fortunately, by following some security best practices now, you can make your site much less susceptible to all manner of attacks, including the elusive zero day threat.
Security tools such as loggers and a firewall can make it more difficult for hackers to use as-yet-undiscovered weak spots against you. We also recommend keeping up-to-date on the latest core, theme, and plugin news, by following popular WordPress blogs and subscribing to specialist mailing lists such as Full Disclosure.
With the right tools, techniques, and resources at your disposal, it’s possible to fend off serious zero day threats. However, your choice of hosting provider also plays a role. At A2 Hosting, we offer several security features to help you ensure that your site is ready for anything, including the unknown!
Image credits: Pexels.
